Hidden in Plain Sight
Anonymebox lets you surf the Internet anonymously from any computer and any mobile device without installing and setting up Tor software on the clients.

Lead Image © Surapong Thammabuht, 123RF.com
Anonymebox lets you surf the Internet anonymously from any computer and any mobile device without installing and setting up Tor software on the clients.
The Tor network provides anonymity on the Internet by creating convoluted paths for sending data. The complexity of the paths makes it impossible for website operators to identify a user by IP address. Anonymebox is a pre-configured Tor router based on the Raspberry Pi. The box directs all data from any connected device through Tor, thereby making it easy to achieve more privacy.
Long before the Edward Snowden leaks, it was clear that almost all of our activities on the Internet are being observed. Observation of Internet activity begins with the web server of the web page provider, where all access to the page is recorded, including time and originating IP address. Additionally, almost all webmasters use analytical tools like Google Analytics, and the Like Me buttons embedded in many websites serve to create detailed user profiles on Facebook, Google, and Twitter. As a consequence, many users want to take back control of their information and seek greater anonymity on the Internet. However, this is not necessarily easy to achieve.
One of the simplest ways to create more privacy is to use Tor, a so-called onion router system [1]. This software directs queries made on the Internet through a veritable forest of servers operated by activists via dynamically created connections. In Tor jargon, each of these way station servers is known as a "node." The anonymization pathway involves three nodes: The data leaves the user's computer in encrypted form and goes to an entry node, where the data is encrypted again and sent on to another Tor node in the network; finally, the data is routed over an exit node and returned to the Internet.
Each of the participating servers in the chain knows only the predecessor and the successor. This arrangement makes it impossible to determine the actual initiator of a connection from any log data that might exist for an identifiable exit node. If at least one of the Tor servers is working reliably and therefore not storing any connection data, then all of the network traffic can be anonymized with Tor. In general, the process depends on end-to-end encryption because the exit nodes are theoretically capable of inspecting all transmitted data. As a consequence, the node could fish access data or passwords out of the data stream.
Although Tor might at first appear to be complicated and inconvenient, it is actually easy to use. The developers offer a Tor Browser [2] that includes a package from the Tor client and a web browser based on Firefox for the user to download, unpack, and start. The default settings for the browser prevent data from being stored in the cache.
The browser is also configured to remove cookies, block plugins like Adobe Flash, and ignore active web content like JavaScript. Otherwise, information about the user would become available in spite of Tor. Tails [3] represents a Live Linux system that fully integrates Tor as well as a series of encryption tools.
The Raspberry Pi distributor pi3g [4] offers anonymebox, which makes the entire process even easier. The anonymebox kit costs EUR100 and consists of a Raspberry Pi 1 Model B, a case, a 16GB SD card with a pre-installed system, network components, and additional USB network cards for WiFi and cable networks (Figure 1). The box lets a computer connect to the Internet via Tor without going over a Tor client. This means, for example, that you can also surf anonymously with mobile devices like smartphones and tablets. Unfortunately, anonymebox does not ship to the US at this time. (See the "Software Only" box.)
Software Only
Pi3g also offers the software for anonymebox on their website [5]. If you have a Raspberry Pi that you are not using, you can turn it into your own anonymebox with the help of software installed via NOOBS instead of buying the branded product from the manufacturer.
 Figure 1: Switch on anonymebox via the USB network card between the computer and router. Alternatively, you can log on to the WiFi access point of the box or use the software-only solution.
Figure 1: Switch on anonymebox via the USB network card between the computer and router. Alternatively, you can log on to the WiFi access point of the box or use the software-only solution.
To begin, you should connect the box to your router using the network cable that is provided; then, plug the USB WiFi module into one of the USB jacks on the Rasp Pi, put in the memory card, and as a final step, connect the box to the power supply unit.
Once anonymebox is completely set up, you can access it by connecting to http://anonymebox.local (Figure 2). The login information for the web front end is preset as admin and password. You should promptly go to Settings and change both of these after your first tests. The front end does not offer any further settings aside from the naming of anonymebox.
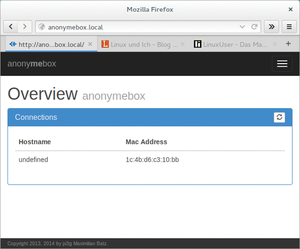 Figure 2: The web front end of anonymebox is used only for changing the login information for the Admin interface and for WiFi access.
Figure 2: The web front end of anonymebox is used only for changing the login information for the Admin interface and for WiFi access.
The WiFi card in anonymebox works in access point mode; therefore, it does not let you create a wireless connection between the box and the router, as would be possible via the network interface of the Raspberry Pi. Instead, the card generates a new WiFi network. If you have not changed the basic setting in the web front end, you should register using the password password with the WiFi network of the box that is called anonymebox.com (Figure 3). Next, you should call up the Tor test page [6] to find out whether your browser has been configured for the use of Tor (Figure 4).
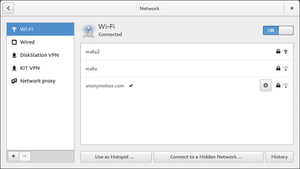 Figure 3: Anonymebox generates its own WiFi network so that mobile devices like smartphones and tablets can surf anonymously.
Figure 3: Anonymebox generates its own WiFi network so that mobile devices like smartphones and tablets can surf anonymously.
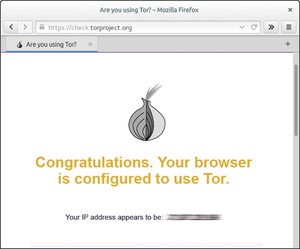 Figure 4: As soon as a connection to anonymebox has been established, the Tor Browser check should notify you that you are surfing anonymously over the Tor network.
Figure 4: As soon as a connection to anonymebox has been established, the Tor Browser check should notify you that you are surfing anonymously over the Tor network.
If your computer is connected by cable to the router and via WiFi to anonymebox, the Tor test page might notify you that the connection does not lead through Tor, even if everything has been correctly set up. The notification message reads, Sorry. You are not using Tor. If you get this message, deactivate the cable network interface so that your system will send any and all data packets via anonymebox.
Now, whatever application you start, anonymebox directs all data packets through the Tor cascade. Websites like Ipinfo.io [7] or Ipleak.net [8] now report that you, or rather your Internet IP, reside in one of several cities – or even in a foreign country. The address that is reported is actually the address for whichever Tor exit node is currently in use. If this happens to be in Holland, then the request for the web server being talked to also comes out of Holland. Tor then directs the data on to you. This is also what happens with mobile devices like smartphones and tablets. If these devices use WiFi from anonymebox to get onto the Internet, they can also be used to surf anonymously (Figure 5).
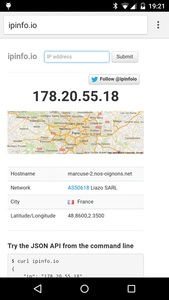 Figure 5: Anonymebox makes anonymous access to the Internet easy. This is especially true for mobile devices like smartphones or tablets because they no longer need special Tor apps.
Figure 5: Anonymebox makes anonymous access to the Internet easy. This is especially true for mobile devices like smartphones or tablets because they no longer need special Tor apps.
The achievable data rates are quite respectable nowadays, thanks especially to the high-performance exit nodes like those from the Chaos Computer Club [9]. When Tor was new, data would often dribble through the net at a speed of 50kbps. However, data is now transported through the network at single-digit megabits per second rates (Figure 6). Even file sharing should be possible with anonymebox and Tor. I achieved transmission rates of up to 1Mbps when running tests on downloads of various Linux distributions (Figure 7).
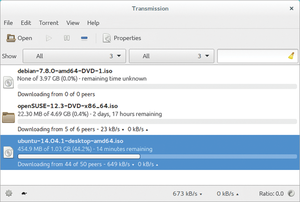 Figure 7: You can even handle P2P file-sharing downloads via the Tor network with speeds of up to 1Mbps, as with the Transmission client here.
Figure 7: You can even handle P2P file-sharing downloads via the Tor network with speeds of up to 1Mbps, as with the Transmission client here.
Not every route through the layers of Tor has such high bandwidth. Because Tor changes the route every 10 minutes, it could become difficult to call up even one website at any time. Depending on the exit node, some pages and servers also refuse to cooperate with your anonymous Internet access. For example, Google blocks some Tor nodes that it deems suspicious (Figure 8). Additionally, many IRC servers do not permit connections originating from the Tor network.
Pages: 4
Price $15.99
(incl. VAT)