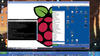
Installing and testing Nextcloud
The free cloud storage software ownCloud has blossomed over the past years into a serious competitor for commercial services like Dropbox and Google Drive. Users can now take responsibility for storing their own data, with convenient synchronization between computers and mobile devices by running a small server outfitted with an ownCloud package. NAS device users can also find easy to install ownCloud packages in the package sources for their system.
However, the ownCloud success story suffered a serious setback at the end of April last year. The ownCloud founder Frank Karlitschek [1] and a number of the original developers all left the project in order to pursue development of a fork which they call Nextcloud [2]. Jos Poortvliet who was previously the Community Manager for ownCloud now handles public relations for Nextcloud. He refers to the undertaking as a "re-start". According to Karlitschek and Poortvliet, this re-start was prompted by dissatisfaction arising out of structural problems and various business decisions in the ownCloud organization.
Separation
As a company, Nextcloud is currently at work with Spreed.me [3]. Spreed.me sells a line of computers named Spreedbox [4]. Each Spreedbox comes with a pre-installed video conferencing solution, created by combining a WebRTC server with ownCloud. Frank Karlitschek and Niels Mache head up the Nextcloud organization itself. Prior to joining Nextcloud, Niels Mache was responsible for Spreed.me and is also a co-founder of Red Hat Germany.
[...]
Buy this article as PDF
Pages: 6
(incl. VAT)